Applies to Platform: UTM 3.0, 4i Edge 3.0, UTM 5.0, 4i Edge 5.0, UTM 6.0, 4i Edge 6.0
Last Update: 21 November 2020
This configuration guide will illustrate how to optimize the IPS engine of the Endian appliance.
Scope: Depending on the infrastructure used, it is important to have an optimized IPS engine so that the resources used are allocated correctly, thus improving the performance, speed and response times of Endian systems within a network.
The first step is to enable, update and configure the IPS engine by clicking the gray button (turned to green when enabled). For details please click How To Enable & Configure The IPS. After this, all the rules are enabled by default and need to be optimized.
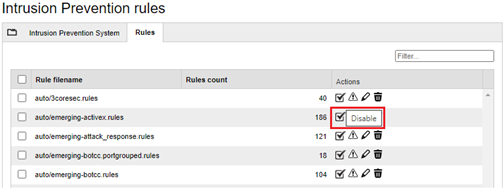
The second step is to identify the components of your infrastructure and define a set of recommended rules to be activated (enabled) and optimized according to your needs, then click on the Apply button. For example:
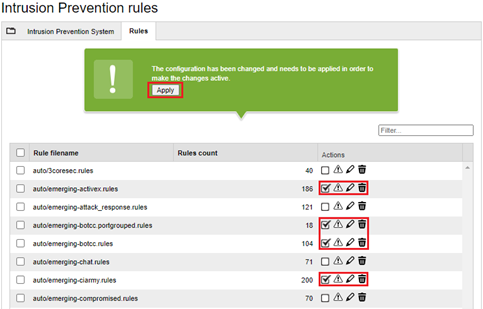
The rules which must be enabled have been classified according to the infrastructure and services which is used and they are structured as follows:
- Default security level
- Additional rules
- ActiveX plugin
- Sensitive or confidential data
- Chats
- Temporary security events
- Web applications and exposed services
- FTP / TFTP services
- Gaming activities
- IMAP protocol
- Mobile devices
- Netbios protocol
- Users activities
- POP3 protocol
- RPC protocol
- SCANDA protocol
- SMTP protocol
- SNMP protocol
- SQL services
- VOIP services
Note
The bold rules and default rules in each section are recommended to be enabled as described in the second step of this article based on the infrastructure that is used.
Default security level
For small and medium infrastructure which contain less sensitive and confidential data and information. This is our recommendation for the IPS default security level ruleset:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
Additional rules
For small and medium infrastructure which contain less sensitive and confidential data and information:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-icmp_info.rules
auto/emerging-inappropriate.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-misc.rules
auto/emerging-telnet.rules
auto/emerging-tor.rules
ActiveX plugin
The infrastructure uses ActiveX plugin in browsers:
auto/3coresec.rules
auto/emerging-activex.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
Sensitive or confidential data. ISO27001 requirements
To be enabled for medium and large infrastructure which contain sensitive and confidential data and information:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-botcc.portgrouped.rules
auto/emerging-botcc.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-policy.rules
auto/emerging-scan.rules
auto/emerging-shellcode.rules
auto/emerging-trojan.rules
auto/emerging-worm.rules
Chats
To be enabled for an infrastructure in which Chats are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-chat.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
Temporary security events
To be enabled for medium and large infrastructures that contain sensitive and confidential data or information when a temporary security event occurred:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-current_events.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
Web applications and exposed services. ISO27001 requirements
For an infrastructure contain webservers, web applications and other services public exposed to the internet:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-botcc.portgrouped.rules
auto/emerging-botcc.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-exploit.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-policy.rules
auto/emerging-scan.rules
auto/emerging-shellcode.rules
auto/emerging-trojan.rules
auto/emerging-user_agents.rules
auto/emerging-web_client.rules
auto/emerging-web_server.rules
auto/emerging-web_specific_apps.rules
auto/emerging-worm.rules
FTP / TFTP services
To be enabled for an infrastructure in which FTP / TFTP services are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-ftp.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-tftp.rules
Gaming activities
To be enabled for an infrastructure in which Gaming activities are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-games.rules
auto/emerging-info.rules
auto/emerging-malware.rules
IMAP protocol. ISO27001 requirements
For an infrastructure in
which IMAP protocol and email services are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-imap.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-smtp.rules
Mobile devices. ISO27001 requirements
To be enabled for an infrastructure in which Mobile devices are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-mobile_malware.rules
Netbios protocol
For for an infrastructure in
which Netbios protocol are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-netbios.rules
User activities. ISO27001 requirements
Rulesets that will be enabled for an infrastructure in which user activities inside the organizations should be monitored and blocked (eg. Torrents):
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-botcc.portgrouped.rules
auto/emerging-botcc.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-p2p.rules
auto/emerging-policy.rules
auto/emerging-scan.rules
auto/emerging-shellcode.rules
auto/emerging-trojan.rules
auto/emerging-worm.rules
POP3 protocol
For an infrastructure in
which POP3 protocol and email services are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-pop3.rules
auto/emerging-smtp.rules
RPC protocol
To be enabled for an infrastructure in which RPC protocol are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-rpc.rules
SCADA protocol
To be enabled for an infrastructure in which SCADA protocol are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-scada.rules
SMTP protocol. ISO27001 requirements
Rulesets that will be enabled for an infrastructure in
which SMTP protocol and email services are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-imap.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-pop3.rules
auto/emerging-smtp.rules
SNMP protocol
To be enabled for an infrastructure in which SNMP protocol are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-snmp.rules
SQL services
To be enabled for an infrastructure in which SQL services are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-sql.rules
VOIP services
Rulesets that will be enabled for an infrastructure in
which VOIP services are used:
auto/3coresec.rules
auto/emerging-attack_response.rules
auto/emerging-ciarmy.rules
auto/emerging-compromised.rules
auto/emerging-dns.rules
auto/emerging-dos.rules
auto/emerging-drop.rules
auto/emerging-dshield.rules
auto/emerging-info.rules
auto/emerging-malware.rules
auto/emerging-voip.rules
RFE (requested feature enhancement): It is not possible to scan just the number under Services > Intrusion Prevention > Rules, so you need to extract it, e.g. from the console (what I did) with
grep -rnw '/var/signatures/snort' -e '2012647'
to find that the rule is in 'emerging-policy.rules' and there I can disable it.
Would it not better that the web admin interface could scan it for me? I think it is :)