Applies to Platform: UTM 5.1
Background
This article illustrates how to configure the Endpoint advanced access policy on the switchboard module.
The access policy is an optional configuration that allows to set specific customs views on the endpoint's application for every user in the system.
Requisites
- Switchboard module installed and configured with the last version of Endian OS or having an account on Connect Switchboard cloud
- at least one Gateway with one Endpoint
- at least one user with "Manage Device" permission
Warning!
Configuration
Considering a Switchboard with the following configuration:
- a Gateway called gateway-milano-01
- three Endpoints called linux, web_portal, windows
- five user that have access to the gateway and the endpoints
Go in the switchboard Device page and edit the Gateway by clicking on the pencil icon ().
Navigate to the Permissions tab and set the user you want to allow to use the endpoint application as "regular user" or "manager" of the Gateway.
After that we can now specify the access policies in the text box called Policies below.
Warning!
The policies rules are text strings having a syntax that imitates the one used by SQL query. The syntax is:
ALLOW/DENY <<application_name>> ON <<endpoint_name>> TO <<user_name>>
The wildcard * is accepted in any position and will indicate any (application, endpoint, user).
The order of the rules will determinate the priority, the first rule matched will be the one to be executed. If no rule is matched the default rule will be
ALLOW *
Everything will be accepted.
In case we want to have full control on the application access for each endpoint the best practice is to set the last rule with
DENY
This will block all the access between application, endpoint, user not directly specify from the policies.
ALLOW 'Secure Shell' ON linux TO bob@acme.com
DENY * ON windows TO alice@acme.com
ALLOW * TO alice@acme.com
ALLOW * ON * TO jon.doe@acme.com
ALLOW 'VNC Remote Desktop' TO eve@acme.com
DENY
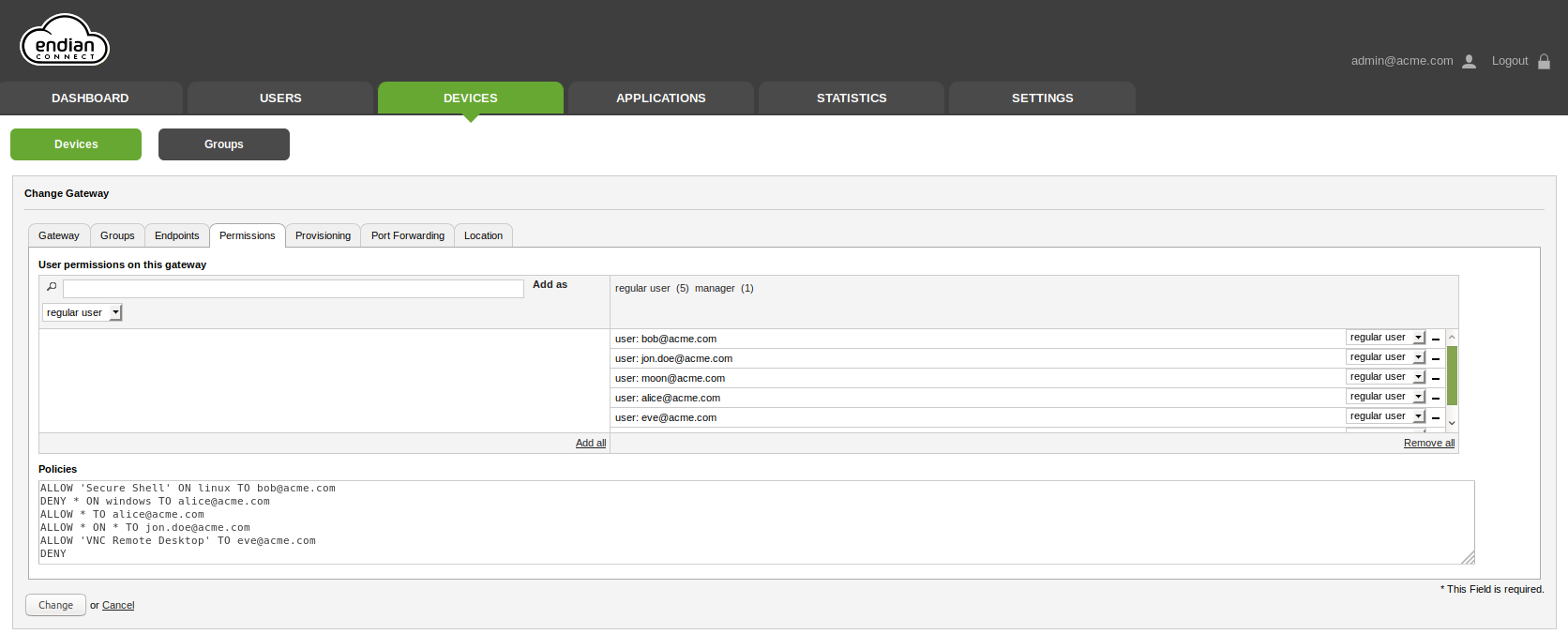
This configuration will allow the following visibility of endpoint and application:
User bob@acme.com will be able to see only the Secure Shell application linux endpoint.
User alice@acme.com will be able to see all applications on any endpoints except the ones on windows endpoint.
User eve@acme.com will be able to see only "VNC Remote Desktop" application on all endpoints but since this Application is available only on the windows endpoint that will be the only application available. In case more endpoints with "VNC Remote Desktop" will be added in future, this user will be automatically able to see them all.
User moon@acme.com will not be able to see any application on any endpoint.
User jon.doe@acme.com will be able to see every application on every endpoints.
Note
ALLOW 'Secure Shell/Organization_NAME' ON Linux-server TO bob@acme.com
Comments