Applies to Platform: Linux
Scenario
This lessons illustrates how to generate a CA, along with a server and a client certificate using EasyRSA from a Linux box. The EasyRSA version used in this lesson is 3.0.5. We will create a certificate/key pair for CA, Server and client.
The server side requires:
- CA certificate, needed to create server and client certificate and used to verify if the client certificate was signed by the master CA (Certification Authority). The CA key must be kept secret.
- Server certificate and key, its own certificate/key. The server will only accept clients whose certificates were signed by the master CA certificate.
The client side requires:
- CA certificate, needed to create server and client certificate and used to verify if the client certificate was signed by the master CA (Certification Authority). The CA key must be kept secret.
- Client certificate and key, its own certificate/key. The client will send to server its own certificate, previously signed by the master CA certificate.
Prerequisites
- PC with Linux OS.
- Easy-RSA package already installed.
- Server and client clocks need to be synced or certificates might not work properly.
CA, server and client certificate creation
1. First of all, we need to fill our personal information that will be written into the certificates. In order to do this, from your EasyRSA folder there should be a vars.example file that will be used as template for a personalized file. Therefore, copy this template to a new file with the command:
root@linux:/your/easyrsa/folder# cp vars.example vars
then open vars file with your preferred text editor, then look for the following lines, uncomment them and fill them properly with your personal information:
Note
set_var EASYRSA_DN "org" # Set to "org" to activate following information request
set_var EASYRSA_REQ_COUNTRY "US"
set_var EASYRSA_REQ_PROVINCE "California"
set_var EASYRSA_REQ_CITY "San Francisco"
set_var EASYRSA_REQ_ORG "Copyleft Certificate Co"
set_var EASYRSA_REQ_EMAIL "me@example.net"
set_var EASYRSA_REQ_OU "My Organizational Unit"
Although in this guide we will stick to default values, other settings that can be personalized can be found into vars file, like custom paths for OpenSSL and generated certificates, RSA and Digest algorithm, and other advanced settings. Stick to vars.example comments for a description of each custom setting.
2. Navigate into Easy-RSA directory and create a new PKI and CA:
root@linux:/your/easyrsa/folder# ./easyrsa init-pki
root@linux:/your/easyrsa/folder# ./easyrsa build-ca
A password will be requested and it will become CA certificate password. After this, CA creation is complete and the command output will tell you where the new CA certificate was created. Below there is an example of command output:
CA creation is complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/your/easyrsa/folder/pki/ca.crt
3. In the same main EasyRSA folder, execute the following commands to create and sign both server and client certificates, using CA certificate created in the previous steps. For issued commands below, CA certificate password previously set to sign these certificates and new password for both server and client certificates will be asked:
root@linux:/your/easyrsa/folder # ./easyrsa build-server-full ServerCert
root@linux:/your/easyrsa/folder # ./easyrsa build-client-full ClientCert
After this, ServerCert.crt and ClientCert.crt are generated into /your/easy-rsa/dir/pki/issued/ folder , among with they respective ServerCert.key and ClientCert.key into /your/easy-rsa/dir/pki/private folder.
4. We need now to export both server and certificate in PCKS#12 format, that will include both certificate and
private key in a single file. For issued commands below, both server and certificate password previously set to sign these certificates and new password for both server and client certificates in PKCS#12 format will be asked:
root@linux:/your/easyrsa/folder # ./easyrsa export-p12 ServerCert
root@linux:/your/easyrsa/folder # ./easyrsa export-p12 ClientCert
After this, each command will give out an output where absolute path of generated PKCS#12 files is given:
Successful export of p12 file. Your exported file is at the following
location: /your/easyrsa/folder/pki/private/ServerCert.p12
Successful export of p12 file. Your exported file is at the following
location: /your/easyrsa/folder/pki/private/ClientCert.p12
Warning
root@linux:/your/easyrsa/folder # ./easyrsa build-client-full NewClientCertand, if you have already imported corresponding CA and server certificates before, to import only the new client certificate into Endian UTM appliance by going directly to step 4 of the next section.
root@linux:/your/easyrsa/folder # ./easyrsa export-p12 NewClientCert
Warning
CA, server and client certificate import
Once all these files were created, we have to import them on Endian UTM appliance. We will start by importing CA certificate into Endian UTM appliance.
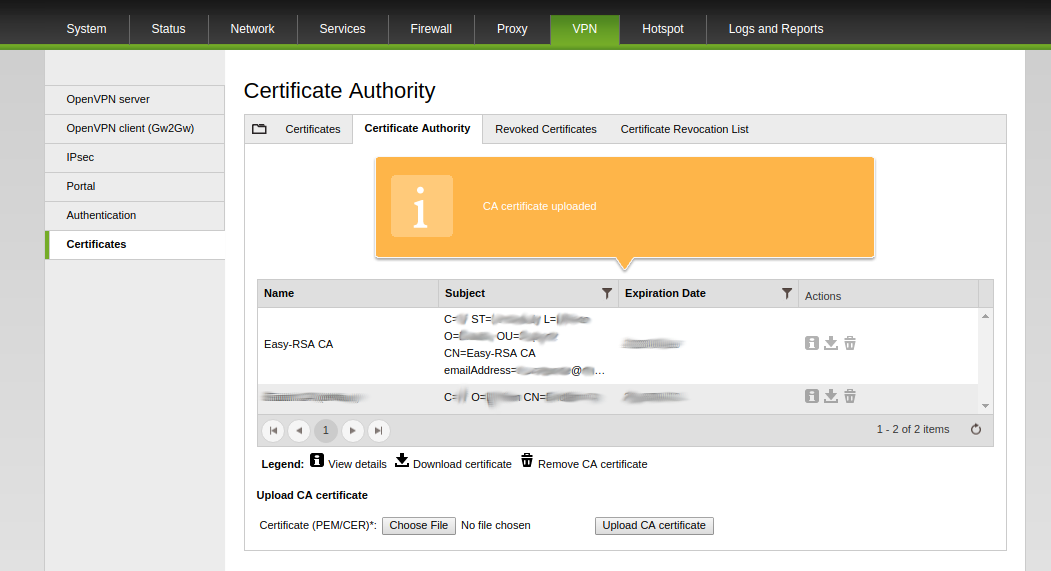
1. Go on Menubar > VPN > Certificates > Certificate Authority, then click on Choose File, select ca.crt certificate generated on step 2 of the previous section and click on Upload CA certificate.

The new CA certificate will appear into the list of registered CA.
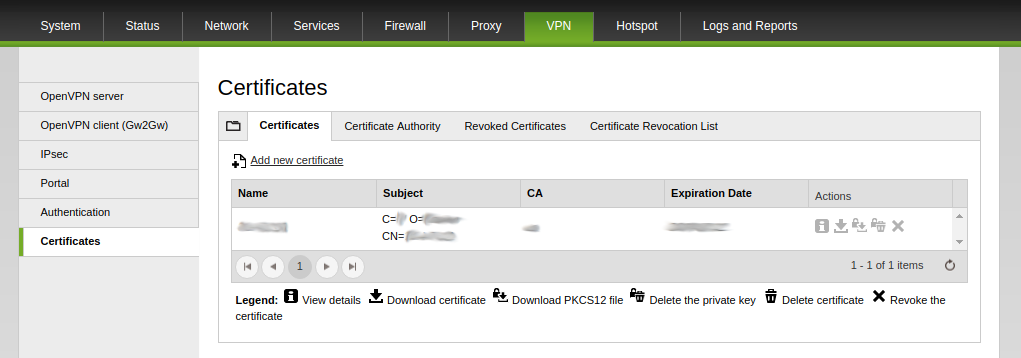
2. Go on Menubar > VPN > Certificates and click on Add new certificate.
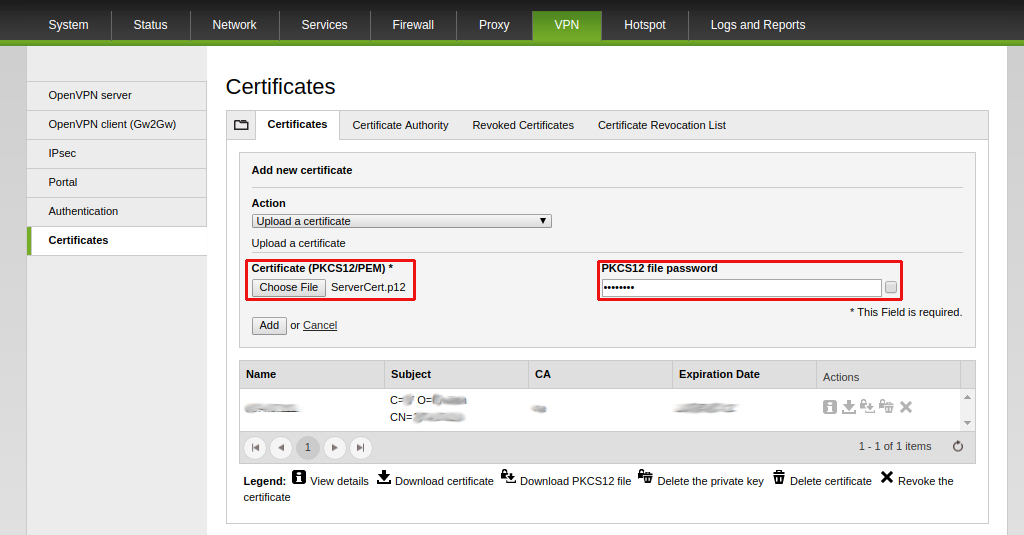
3. Under Action, select Upload a certificate, then click on Choose file, select ServerCert.p12 file and type PKCS#12 file password as set on step 4 of the previous section, and click on Add.
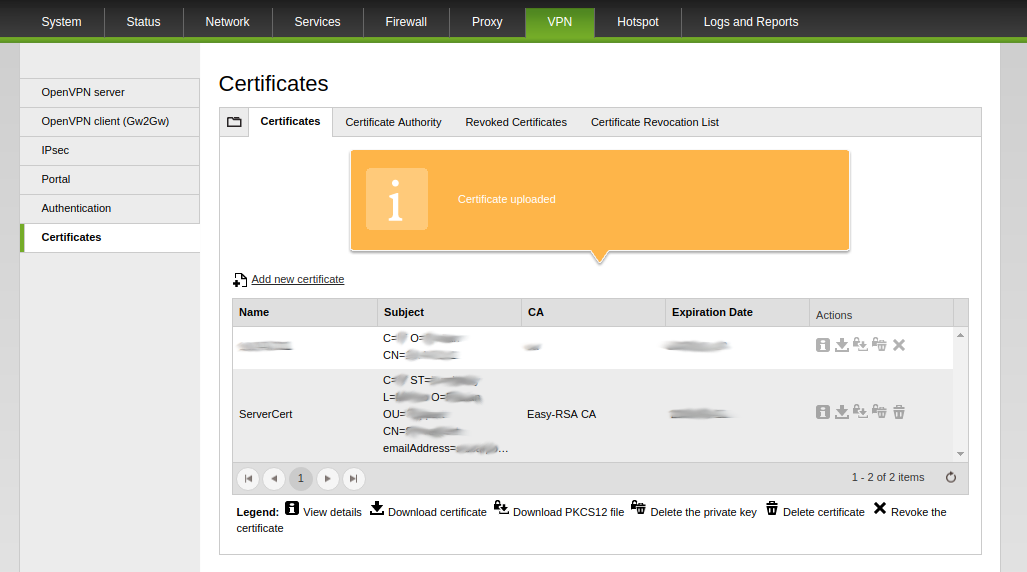
The new server certificate will appear into the list of registered certificates.
4. Go on Menubar > VPN > Authentication and click on Add new local user.
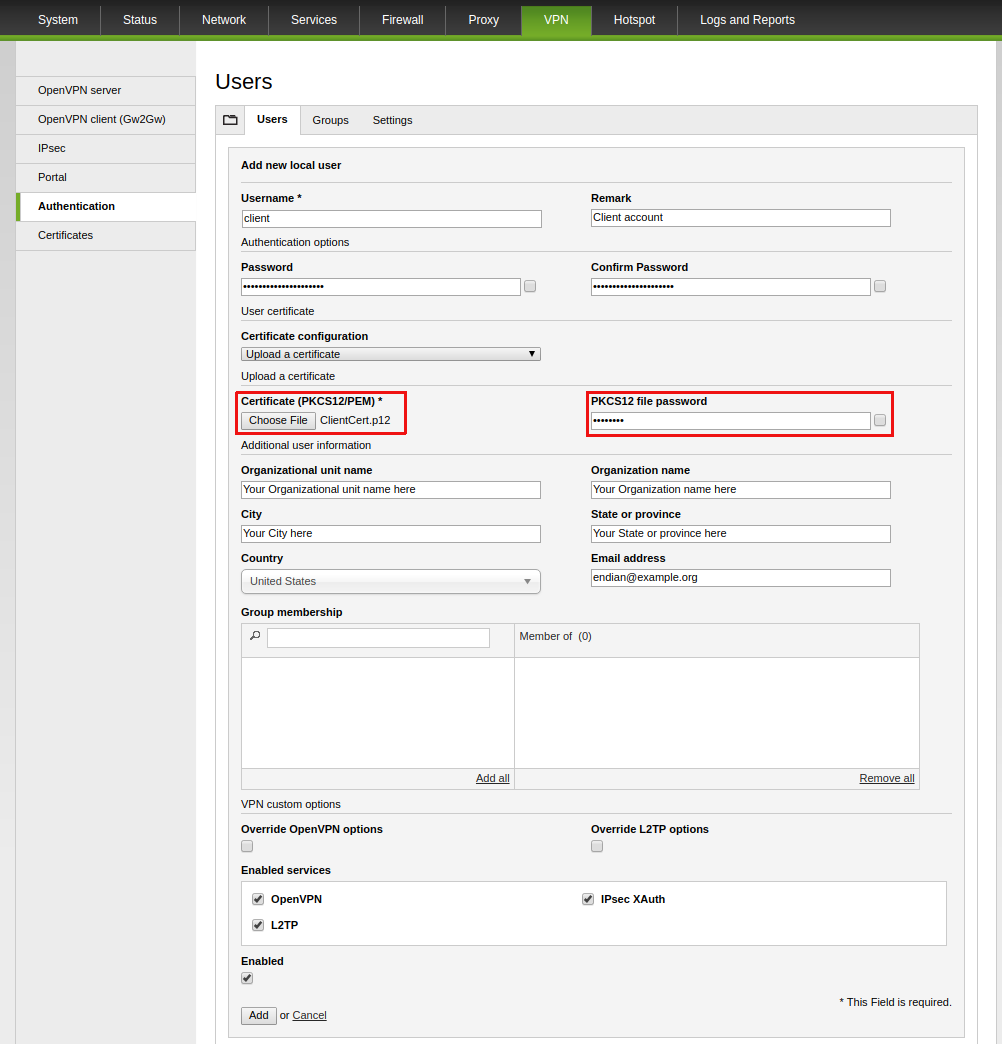
5. Fill properly the form with your information, select Upload a certificate,then click on Choose file, select ClientCert.p12 file and type PKCS#12 file password as set on step 4 of the previous section and click on Add.
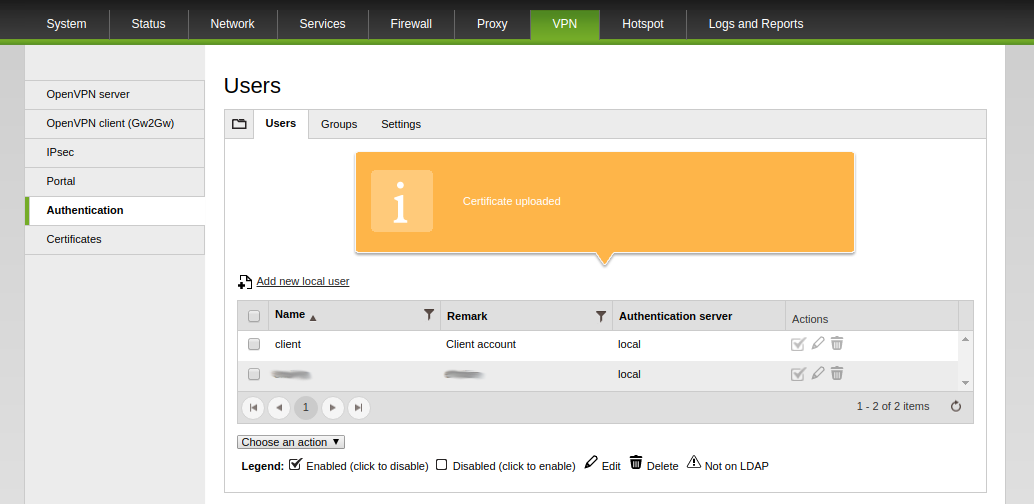
The new user with corresponding client certificate will appear in the list, while the new client certificate will appear into the list of registered certificates under Certificates voice.
Now it is possible to use this server certificate for any server instance which can adopt certificate authentication on Endian UTM appliance (OpenVPN, IPSec/L2TP, VPN Portal, ecc.), while the corresponding client certificate will be used by the client who wants to connect to that particular server instance.
Comments