Applies to platform: UTM 2.5 , 4i 2.5
Last updated: 5th November 2012
This lessons introduces you to Trusted Timestamping (TTS) and guides you in its activation on the Endian UTM Appliance.
Trusted Timestamping is a process that log files (but in general any document) undergo in order to track and certify their origin and compliance to the original. In other words, trusted timestamping allows to certify and verify that a log file has not been modified in any way by anyone, not even the original author since it wass generated. In the case of log files for example, TTS proves useful to verify the accesses to the system or the connections from the users of your hotspot, even in cases of independent audits.
Requirements
In order to activate TTS, you need:
- An Endian UTM Appliance which supports Trusted Timestamping.
- A valid URL of a valid Time Stamping Authority (TSA). Note that this is usually a commercial service, that several Companies can supply.
- An username and password (optional) to access the service, provided by the TSA
- The TSA server's publick key (optional).
How Trusted Timestamping works
The timestamping process starts only after the log files are rotated for the first time after the activation of the trusted timestamping service. Usually, logrotate runs once nightly, so the next day it will be possible to verify that the log files have been certified. When the log files are rotated, the TSA client calculates a hash value for each log file, and sends it to the TSA, which signs this value and returns it to the client. The signed value will be used to verify that the log file has not been corrupted or modified in any way, but it is exactly the same as it was created and signed. The idea is that whenever a file is modified, even slightly, its hash value changes considerably, so even adding a single character will completely modify the file’s hash code.
Do not forget:
- None of the log files is sent to the TSA, only their hash value.
- The first time that the trusted timestamping service is active, only the hash values of the previous day’s log files are sent to be signed. To sign all the log files present in your appliance, enter the CLI via SSH (or use the web console, Menubar > System > Web Console) and issue the following command:
root@endian:~ # /usr/local/bin/timestamp_log_archives -df
Enabling Trusted Timestamping on your Endian UTM Appliance
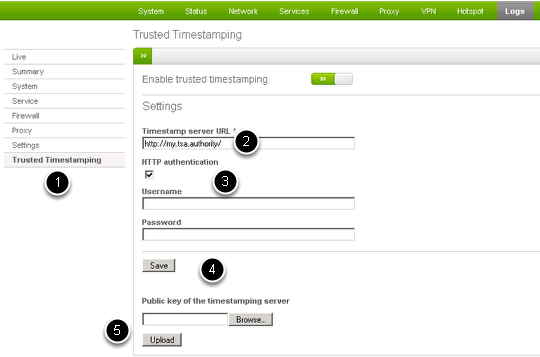
Trusted Timestamping activation requires only a few minutes.
- Go to Menubar > Logs > Trusted Timestamping.
- Enter the URL provided to you by the TSA.
- Tick the checkbox under HTTP authentication and enter the username and password, if you need to use authentication.
- Click on Save to save your settings
- If you need to use the TSA's public key, browse your computer to find it, then click on Upload to store in on the Endian UTM Appliance.
Verification of the signatures
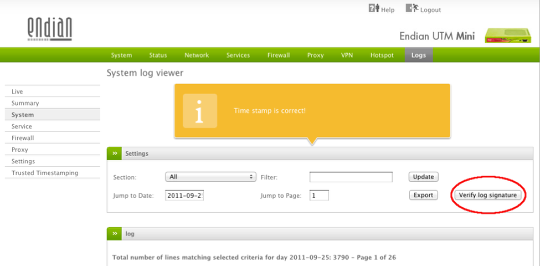
Once the Trusted Timestamping has been activated and log files are signed, a button appears on the right-hand side of the Logs' module. Log files can then can be verified simply by selecting them and clicking on the Verify log signature button.
Comments