Applies to platform: Any device running iOS.
This lesson describes how to connect a smartphone or tablet device to an existent and running IPsec installation on the Endian UTM appliances using PSK (password) authentication.
Note
The connection via L2TP/IPsec requires the following data, that should have been previously configured on the VPN/IPsec server:
- The IP address or hostname of the L2TP/IPsec server (i.e., of the Endian UTM appliances where the IPsec server runs).
- The PSK secret, i.e., the password of the IPSsec tunnel, that can be retrieved under Menubar > VPN > IPsec, by clicking on the Edit icon next to the connection, and then looking in the Authentication box.
- The username and password of the L2TP user. The username is retrievable from Menubar > VPN > Authentication, and the user must be allowed to use L2TP.
You should write the above mentioned data down or remember it, since you will have to enter them in the corresponding configuration sections of your device.
Setup of a VPN connection to the Endian UTM Appliance

To configure your Apple device, e.g., iPhone or iPad, you need first to go under Settings > General > VPN, then tap on Add VPN connection.
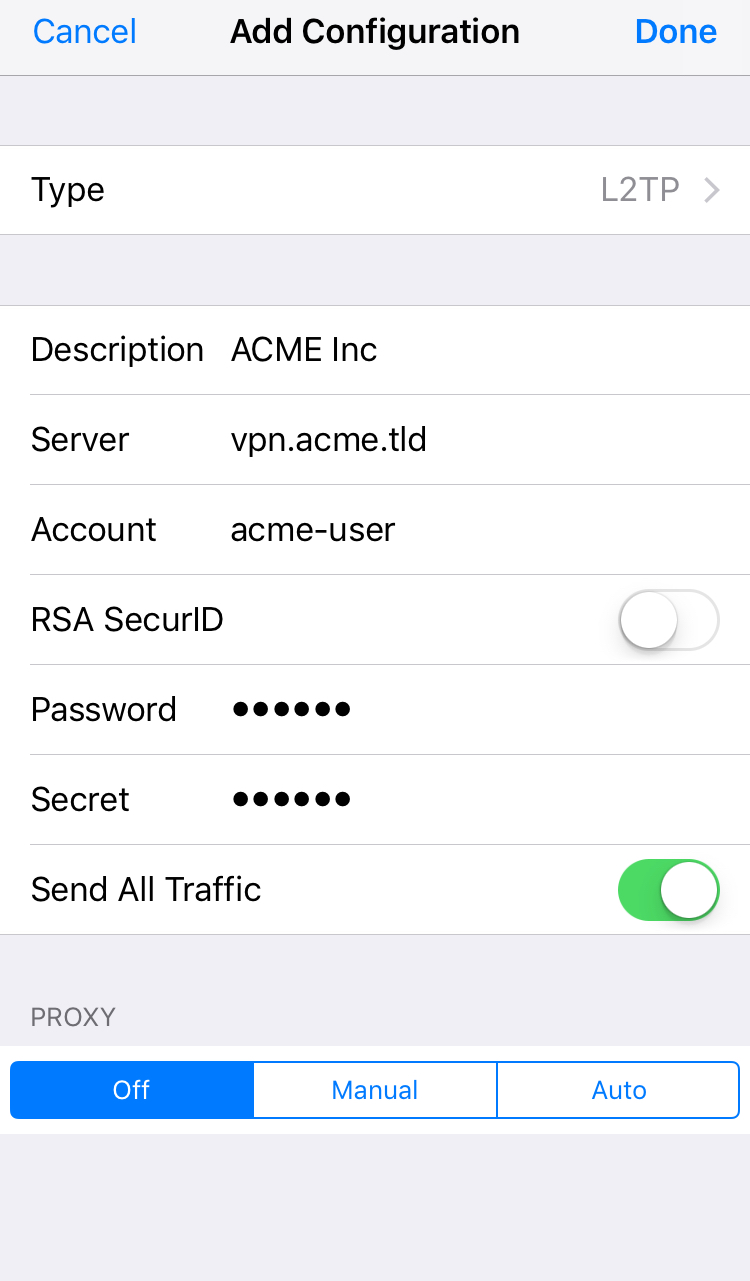
In the configuration window for the VPN connection, carry out the following operations:
- Select L2TP as Type.
- Enter a custom description for the connection. This is the name that will be displayed in the list of available VPN connections.
- Enter the IP address or hostname next to Server.
- Tap on Account and enter your username.
- If you want to store your password on the device, tap Password and enter your password.
- Tap Secret and enter your PSK Secret.
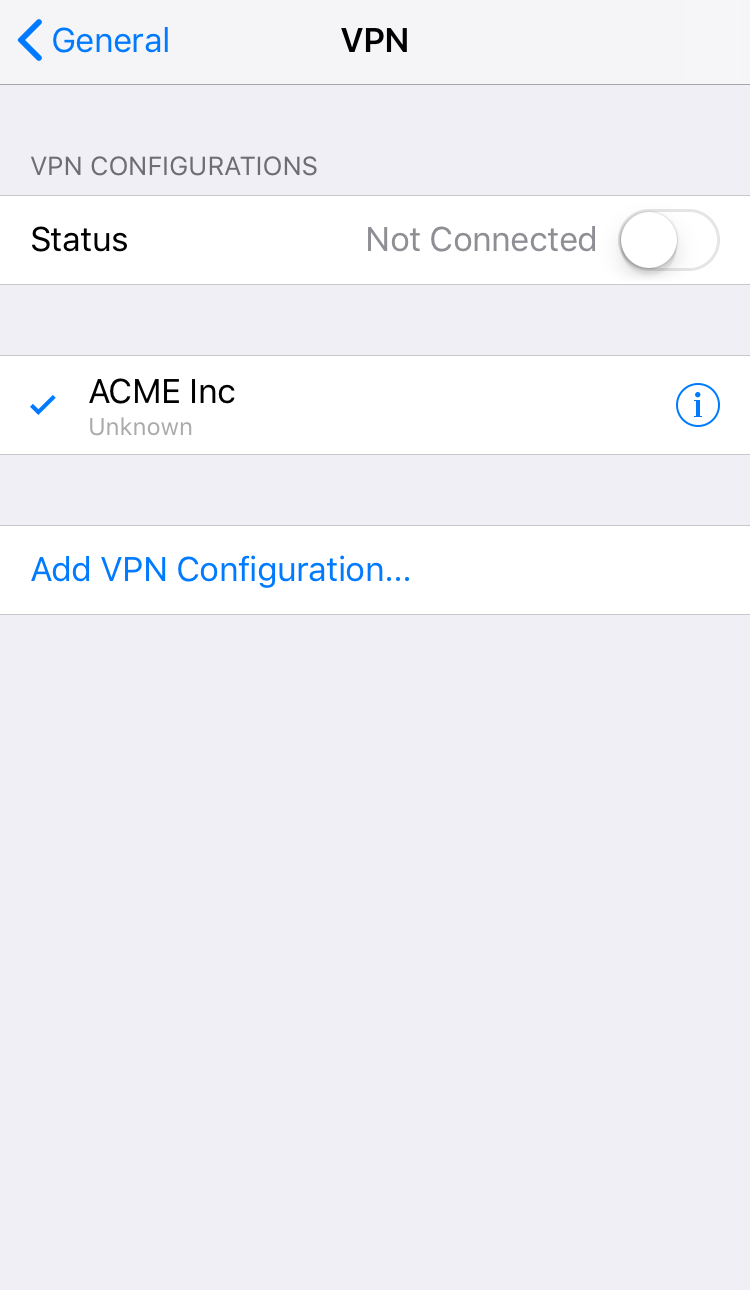
When the configuration has been ended, in the VPN menu, slide to ON the VPN switch to start the connection.
Ho provato e riprovato ma non riesco a far funzionare il collegamento, l'endian è configurato come riportato nella guida http://endian.zendesk.com/entries/21129081-Setup-of-a-VPN-with-IPsec-and-an-L2TP-tunnel
Consultando i log di sistema sembra che la connessione IPSec vada a buon fine ma non la L2TP e di seguito si chiude anche la IPSec
Incollo l'ultima parte dei log laddove sembra manifestarsi il problema:
Apr 12 11:32:28 xl2tpd[23845] network_thread: recv packet from X.X.X.X, size = 78, tunnel = 0, call = 0 ref=0 refhim=0
Apr 12 11:32:28 xl2tpd[23845] get_call: allocating new tunnel for host X.X.X.X, port 49218.
Apr 12 11:32:28 xl2tpd[23845] handle_avps: handling avp's for tunnel 39265, call 27462
Apr 12 11:32:28 xl2tpd[23845] message_type_avp: message type 1 (Start-Control-Connection-Request)
Apr 12 11:32:28 xl2tpd[23845] protocol_version_avp: peer is using version 1, revision 0.
Apr 12 11:32:28 xl2tpd[23845] framing_caps_avp: supported peer frames: async sync
Apr 12 11:32:28 xl2tpd[23845] hostname_avp: peer reports hostname 'iPhone5'
Apr 12 11:32:28 xl2tpd[23845] assigned_tunnel_avp: using peer's tunnel 19
Apr 12 11:32:28 xl2tpd[23845] receive_window_size_avp: peer wants RWS of 4. Will use flow control.
Apr 12 11:32:28 xl2tpd[23845] control_finish: message type is Start-Control-Connection-Request(1). Tunnel is 19, call is 0.
Apr 12 11:32:28 xl2tpd[23845] control_finish: sending SCCRP
Apr 12 11:32:31 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:32 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:32 xl2tpd[23845] network_thread: recv packet from X.X.X.X, size = 78, tunnel = 0, call = 0 ref=0 refhim=0
Apr 12 11:32:32 xl2tpd[23845] get_call: allocating new tunnel for host X.X.X.X, port 49218.
Apr 12 11:32:32 xl2tpd[23845] handle_avps: handling avp's for tunnel 61409, call 27074
Apr 12 11:32:32 xl2tpd[23845] message_type_avp: message type 1 (Start-Control-Connection-Request)
Apr 12 11:32:32 xl2tpd[23845] protocol_version_avp: peer is using version 1, revision 0.
Apr 12 11:32:32 xl2tpd[23845] framing_caps_avp: supported peer frames: async sync
Apr 12 11:32:32 xl2tpd[23845] hostname_avp: peer reports hostname 'iPhone5'
Apr 12 11:32:32 xl2tpd[23845] assigned_tunnel_avp: using peer's tunnel 19
Apr 12 11:32:32 xl2tpd[23845] receive_window_size_avp: peer wants RWS of 4. Will use flow control.
Apr 12 11:32:32 xl2tpd[23845] control_finish: message type is Start-Control-Connection-Request(1). Tunnel is 19, call is 0.
Apr 12 11:32:32 xl2tpd[23845] control_finish: Peer requested tunnel 19 twice, ignoring second one.
Apr 12 11:32:32 xl2tpd[23845] build_fdset: closing down tunnel 61409
Apr 12 11:32:33 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:34 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:35 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:35 xl2tpd[23845] Maximum retries exceeded for tunnel 39265. Closing.
Apr 12 11:32:35 xl2tpd[23845] Connection 19 closed to X.X.X.X, port 49218 (Timeout)
Apr 12 11:32:36 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:37 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:38 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:39 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:40 xl2tpd[23845] network_thread: select timeout
Apr 12 11:32:40 xl2tpd[23845] Unable to deliver closing message for tunnel 39265. Destroying anyway.
Dove sto sbagliando ?