Applies to platform: UTM upto 5.1
Last updated: 4th June 2014
The Endian UTM Appliance is a true firewall in the sense that, besides inter-zones traffic filtering it does also incoming and outgoing filtering through the RED interface. By default the only allowed internet communication (port/protocol) are the following:
- HTTP
- HTTPS
- FTP
- DNS
- POP3
- SMTP
- IMAP4
Any other protocol is disabled by default.
This lessons helps you define a custom firewall rule to allow a protocol (i.e., an application using a given protocol) to access the Internet.
Note
Create a New Rule
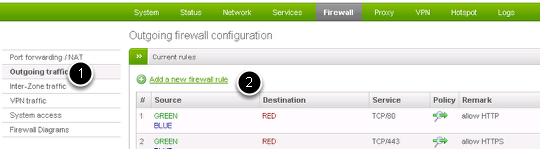
To allow an outgoing Internet communication from the Endian UTM Appliance (apart from using the application proxies), you will need to define proper rules in the outgoing firewall. Dozens among the most used protocol/port are available on the Endian UTM Appliance to chose from. Our example will explicitly allow the MSN Messenger protocol to access the RED Zone from the GREEN:
To open the rules' editor and setting up the new rule, you should:
- go to Menubar > Firewall > Outgoing Firewall.
- Click on Add a new firewall rule.
Define a Rule

The following data should be entered to allow MSN Messenger to access to and to communicate with the Internet (RED) from all devices in the GREEN zone:
- Choose the Zone/Interface as the Source from which to allow MSN Messenger, then click on GREEN chose from the available values. You can supply more than one values by entering one value per line or holding CTRL pressed while clicking the available values.
- Choose <RED> as the Destination interface.
- Scroll down the Service drop-down menu until you see MSN Messenger and select it. The Protocol and Destination port will be filled in with the corresponding values, TCP and 1863 respectively (If you were looking for a service that is not in the list, you can choose User defined as Service, then chose the protocol used by the service, and finally the port(s) needed).
- Chose which policy to apply to all packets that match the rule: Allow makes no control on the traffic, Allow with IPS uses snort, if it is enabled, to check the packets for possible threats.
- Enter an optional remark about the rule.
- Choose at which position to insert the rule (in this case First, but not necessarily). The lower is the rule ID, the higher its priority (i.e., in the image below, the new rule is rule ID 1 and is applied to traffic flow before rule ID 2, rule ID 3, and so on.
- Tick the checkbox next to the Log all accepted connections label to log all the packets that match the rule, but beware that the log size may dramatically increase.
- Click on Create rule to save the rule.
At this point the Rules' editor is closed and you will be brought to the previous screen and see a green callout on top of the list of rules:
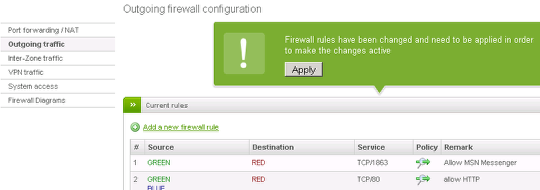
Finally, click on Apply to restart the firewall. If everything went flawlessly, a yellow callsout informs you about the successful completion.
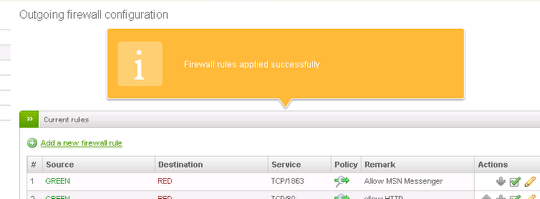
Now, all the required firewalling scripts are restarted and in a few moments the new rule is applied. You can now test it by launching MSN Messenger and chat with your firends.
Great thank you for this,
i have application using port 17857 to communicate to outside,
i've followed your steps but it still not working !
its Utorrents application,