Applies to Platform: UTM 2.4 and 2.5, 4i Edge 2.5
Last Update:9 April 2014
Applies to Platform: UTM 3.0, 4i Edge 3.0, UTM 5.0, 4i Edge 5.0
Last Update:9 April 2014
This lesson will illustrate the necessary steps to configure a very simple Source NAT (SNAT) on a typical Endian appliance. The primary purpose of Source NAT is to take an internal application (IP and port) and manipulate which external IP and/or port is masqueraded to the Internet. By default, the Endian will masquerade all outbound connections to the primary Red interface IP address so you need SNAT in instances where you don't want this to occur.
Configuration Example
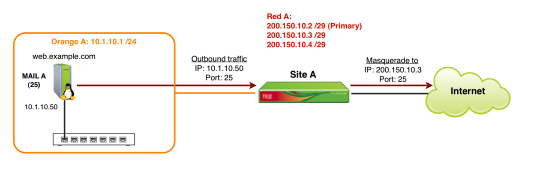
In this simple example, we'll setup a Source NAT (SNAT) for an mail server in the Orange (DMZ) network. We'll use one of our (non-primary) statically assigned public IP addresses as our masqueraded IP.
Create SNAT Rule
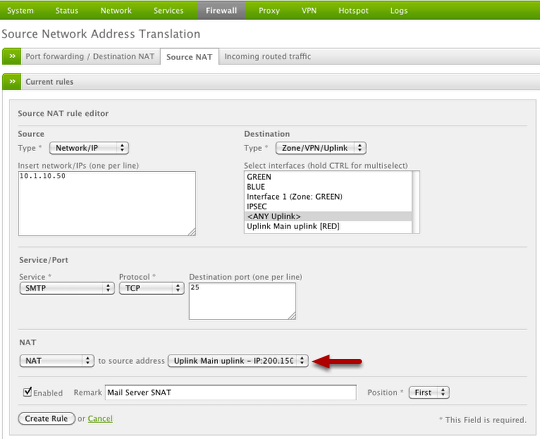
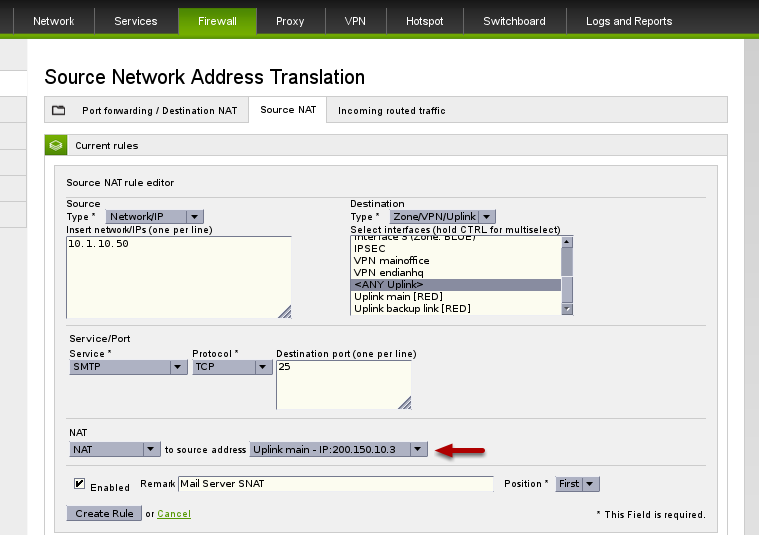
We'll begin by creating a new SNAT rule at which point we can configure all the necessary fields to correspond to our example network. Notice in the "NAT to source address" dropdown we specifically select our new public IP address to use for masquerading for this rule.
Once done, click the Create Rule button.
Apply the Rule
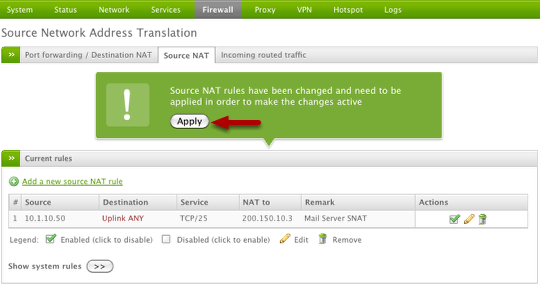

Once your rule is created, you must apply the rule to the device by clicking the Apply button (shown above).
Verify the Rule
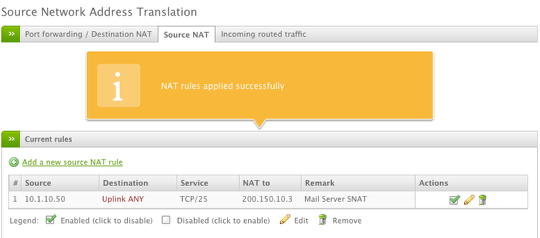
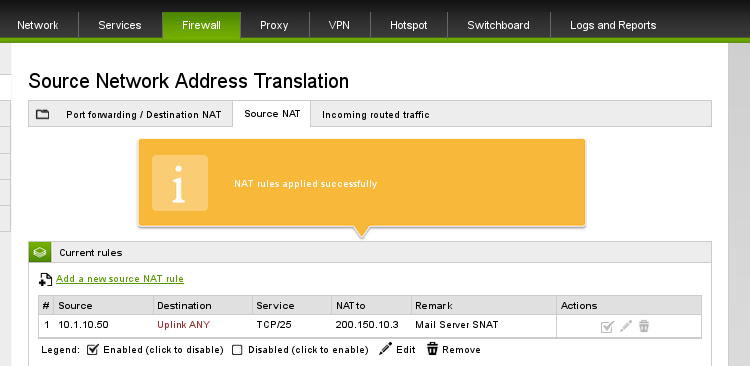
Now that our rule has been applied successfully, we can test that our mail server is being masqueraded to the correct IP address.
Note
root@endian:~# detectip
80.81.82.83
root@endian:~#
Still valid for 2.5