Applies to platform: All (if the necessary services are installed)
Last updated: 14 April 2017
This article quickly introduces what Ransomware and CryptoLocker are, then introduces a number of possibilities to protect your Network from them using an Endian Device.
Note
If your Endian Appliance is equipped with an older version like the 2.5, we urge you to upgrade at least to the 3.0, because you are vulnerable to those kind of attacks.
What is (encrypting) Ransomware like CryptoLocker?
Ransomware is a form of fraud used to obtain money from the victim, whose devices have been blocked using some kind of malware (malicious software), forbidding any access to data.
Encrypting Ransomware is a form of malware that installs on a device's hard disk and encrypts all of its content, making it inaccessible to the device's user until he pays a ransom. CryptoLocker is one of the most 'popular' examples of ransomware and uses RSA public key cryptography.
Ransomware spreads usually disguised within what appears to be legitimate content, like, e.g., an invoice as email attachment, a zip file containing photos, or other types of file that are open by the potential victim since it is not perceived as a dangerous operation. When opened however, the ransomware contacts their so-called Command and Control (C&C) server, which are in charge of generating a new RSA key pair (private/public), storing the private key, and send the public key back to the victim's PC and encrypts everything he can find on the disk and on resources that can be accessed on the local network. At this point, the data can not be accessed anymore, unless they are decrypted with the private key, which however is only available on the C&C server.
Indeed, due to the size of the keys (2048 bits) used for encryption, indeed, it is not feasible to try to decrypt the encrypted files without the private key: While possible in theory, this would take years on average. Therefore, the only way to regain access to the data is either to reinstall all the infected devices and restore a backup, or to pay a ransom and hope to receive the private key (although many victims maintain that they did not receive any key even after they paid).
If you are already infected, you can check the website https://www.nomoreransom.org/ for free decryption keys or simply to find more information on ransomware.
Finally, remember to keep all your systems (not only Endian devices, but all your infrastructure) constantly up-to-date and make sure your team co-worker know about the danger of ransomware and how to avoid opening potentially malicious Web pages or attachments. Preventing threats is always the best solution!
Use your Endian to protect your network from Ransomware
While there is no direct protection offered by Endian devices against ransomware in general, and especially against CryptoLocker, this article presents a collection of methods to intercept and minimise those threats, by blocking the channels used by attackers to spread the infection.
Most of these methods can be deployed on all Endian platforms, while other, which are based on an advanced use of the HTTP and SMTP proxies, are available only on UTM.
1) Using Panda Antivirus
Panda antivirus stores its signatures in the cloud, so you are always guaranteed to use the most recent ones, including those that identify and block any infected vector. By using Panda Antivirus all the checks are made in real time with the latest available signatures.
To enable either antivirus, go to Services > Antivirus engine, then choose the Panda as the antivirus engine, then go to the Panda AntiVirus tab to configure the antivirus.
Note
2) Using the IPS service
The Intrusion Prevention system can not only detect but also block the traffic generated from CryptoLocker to their C&Cs.
To allow the protection with IDS, go to Services > Intrusion Prevention > Rules. Here, search for the auto/emerging-trojan.rules ruleset, which is located in the second page, and change its policy from alert to drop by clicking on the  icon, which will become
icon, which will become 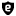 , like in the following screenshot.
, like in the following screenshot.
Now, all the traffic detected as trojan will be dropped. You can also block the auto/emerging-tor.rules for additional protection.
Note
3) Using the outgoing firewall
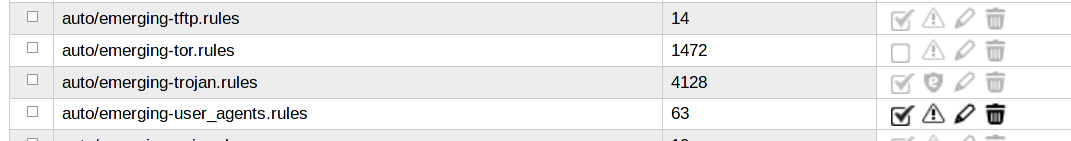
CryptoLocker uses Torrents as infection vector and TOR connections to connect to its C&Cs, therefore another protection is to block all the outgoing traffic that uses these two protocols.
Go to Firewall > Outgoing traffic and create a new rule with policy reject or deny to block this outbound traffic. For a better protection, add all of the networks or zones that lay behind your Endian device by specifying <ANY> in the Source Type.
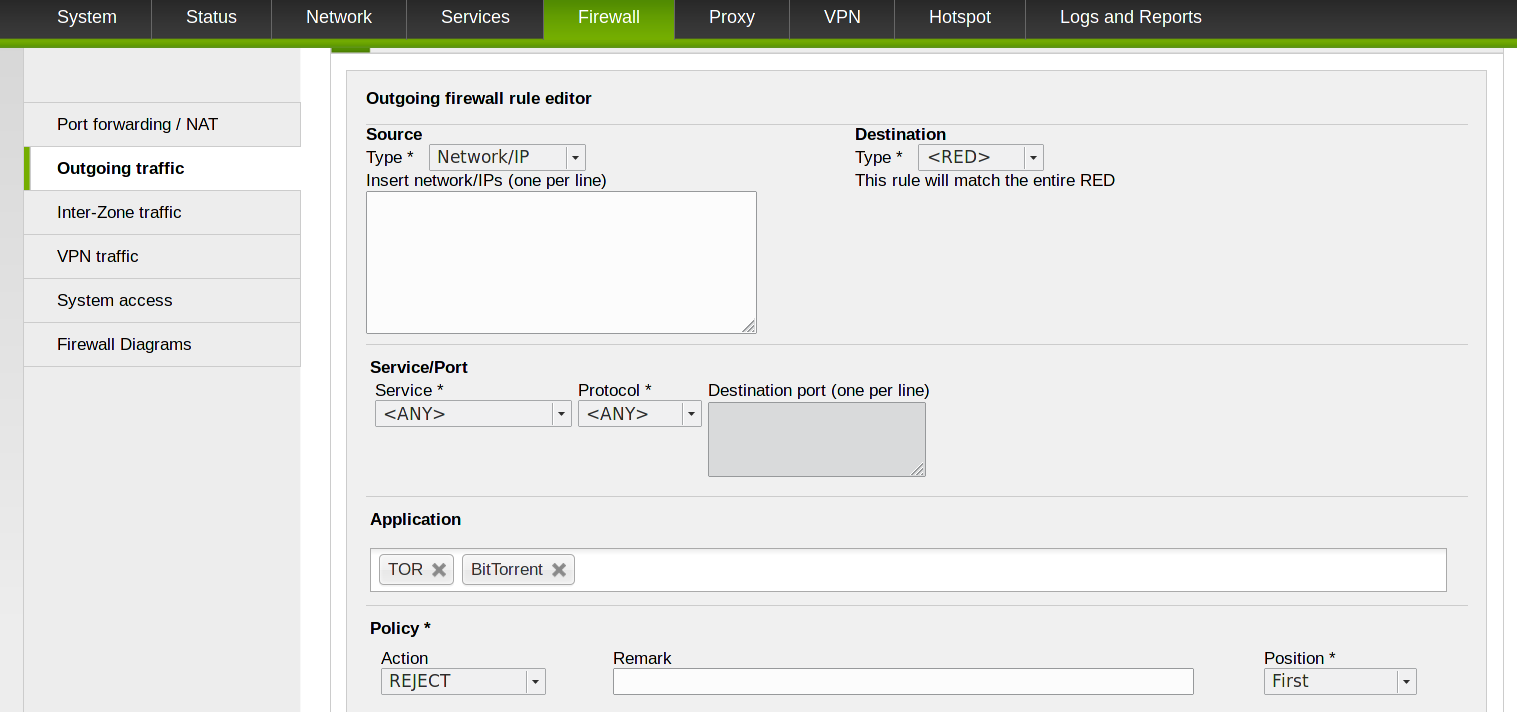
This rule should be the first in the list.
4) Use the HTTP Proxy 1/2: URL Filter
Specify a profile in the HTTP Proxy that blocks malicious URLs that could propagate ransomware.
Go to Proxy > HTTP Web Filter and either modify an existing profile or add a new one. Then, go to the URL Filter part and choose the relevant categories.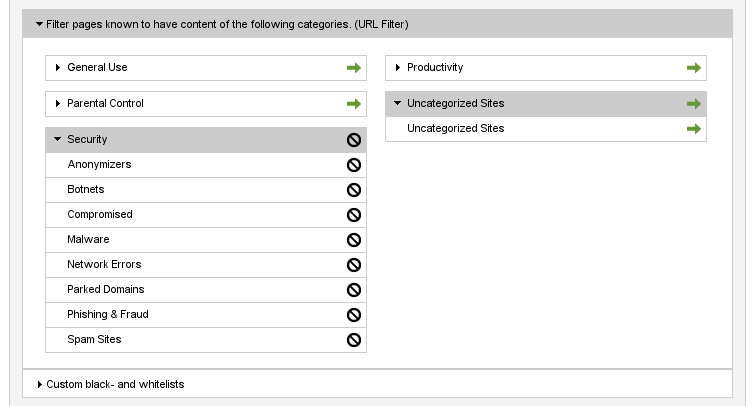
Note
This method can be used together with the next one.
5) Use the HTTP Proxy 2/2: HTTP antivirus scan
The HTTP antivirus scan is active by default, and it is a good practice to keep it enabled.
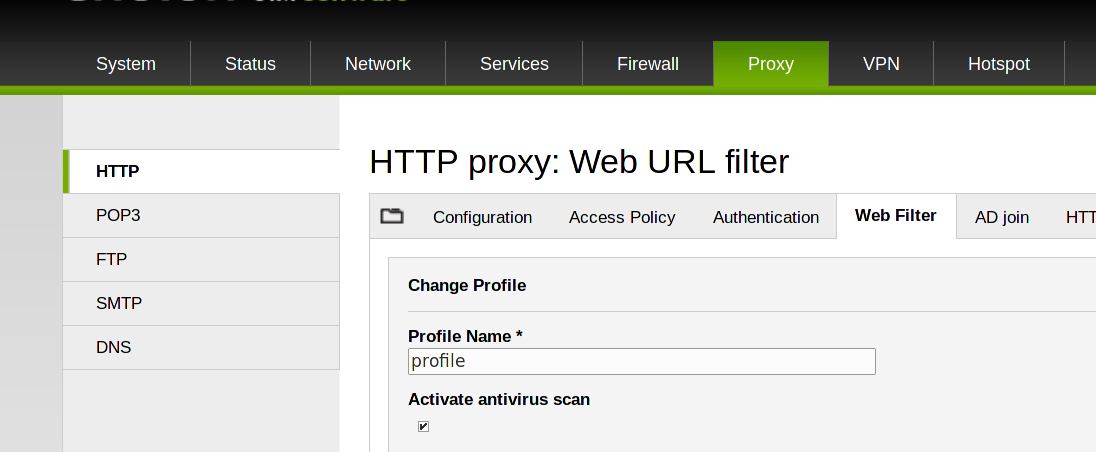
6) Enabling HTTPs proxy
Infection vectors often use HTTPS connections to propagate, therefore the HTTPS proxy can be used to intercept connections and allow only the legitimate connections to well-know sites, like e.g., home-banking providers.
After you have enabled The HTTP Proxy under Proxy > HTTP (the HTTPS proxy must be enabled in conjunction with the HTTP Proxy), go to the HTTPS Proxy tab and tick the Enable the HTTPS Proxy.
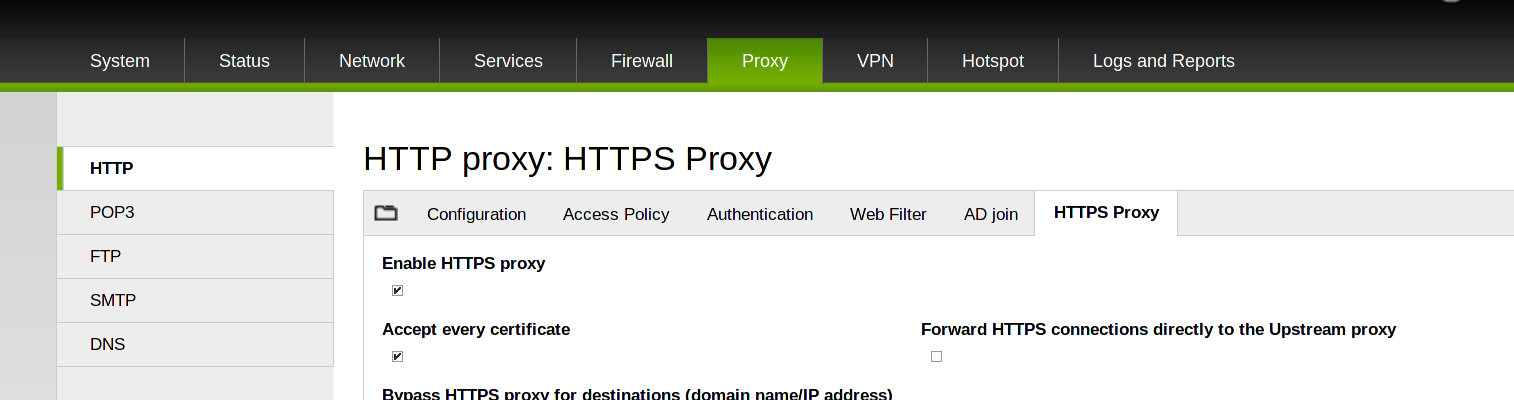
7) Enable SMTP 1/2: antivirus scanning
Ransomware often is delivered as attachments to emails that at a first sight may appear to come from legitimate senders, but contain either a forged link or an attachment that might appear genuine, so a good practice is to activate antivirus scanning of the SMTP Proxy.
Go to Proxy > SMTP and enable it, then in the Virus settings panel tick the checkbox next to the Scan mail for virus label to activate the antivirus scan. You can also configure what to do with an email that has been marked as spam and some additional options.
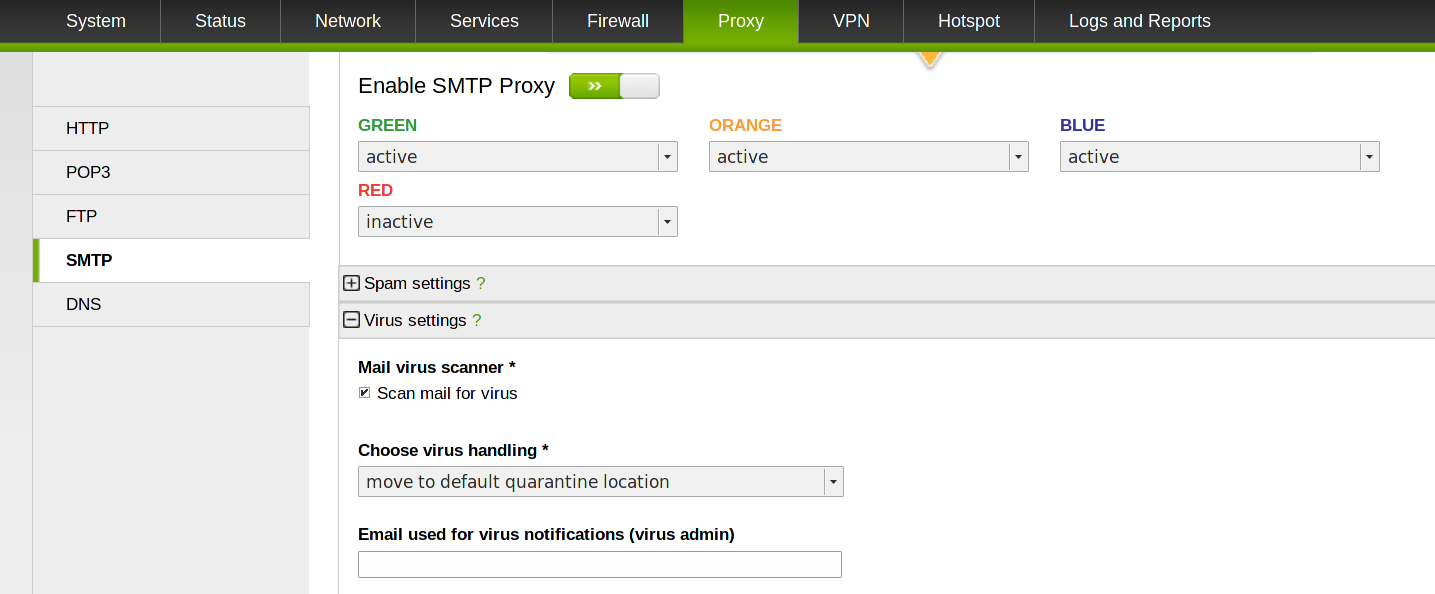
Once done, click on Save to store the new configuration, then on Apply in the green callout to reload the SMTP Proxy with the new options.
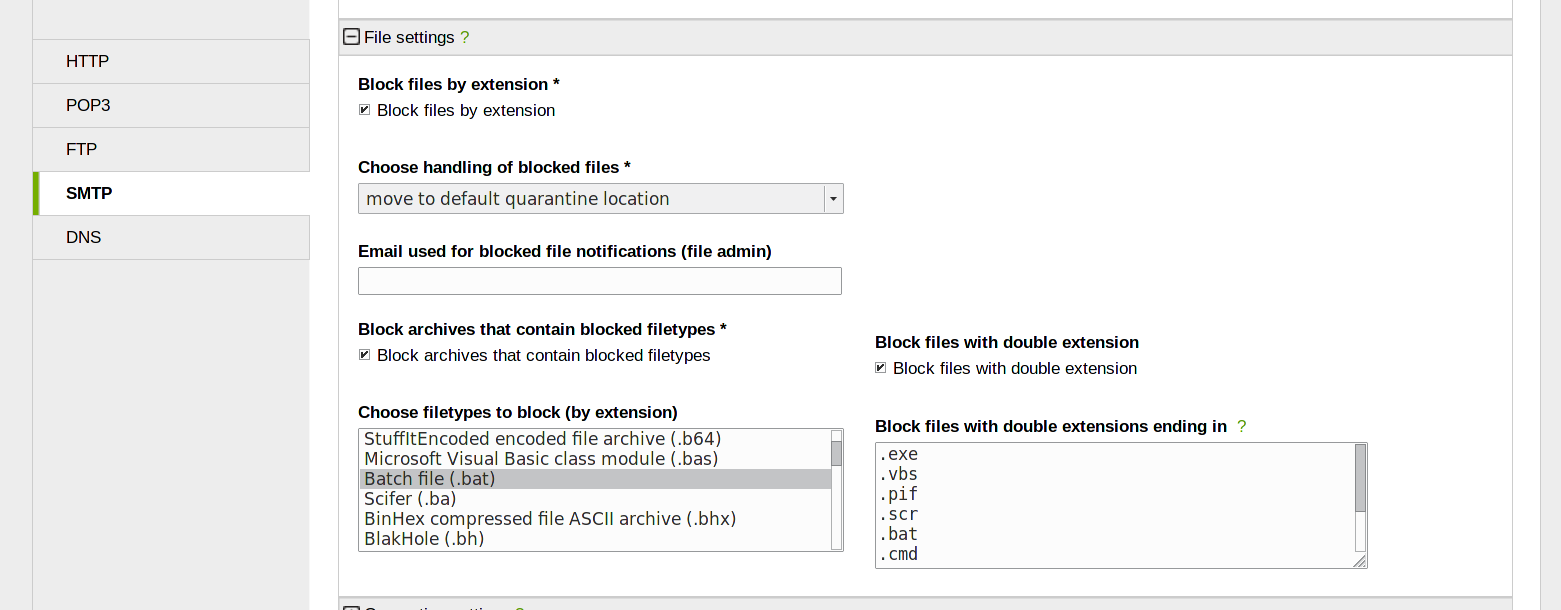
8) Enable SMTP 1/2: File extension and double extension
Another subtle method to deliver ransomware as attachment is to name the attachment with a double extension (e.g., meeting.png.bat), which causes an email client to display only the first extension (e.g., meeting.png), leading the reader to think he received an image. A double click on it will however not cause to the "image" to be displayed, but the batch file to be executed, without the user noticing, except for the "image" not shown on the monitor. Therefore, another good practice is to block potentially dangerous file extensions (like e.g., .bat, xlsx, docx) and forbid attachment whose name has two extensions.
Go to Proxy > SMTP and enable it, then in the File settings panel tick the checkbox next to the Block files by extension label to activate the emails' attachments to be checked.
Then in the Choose filetypes to block (by extension) box, select all the extensions that should be blocked by the SMTP Proxy, then tick the checkbox next to the Block files with double extension label and select from the drop-down menu that will appear all the extensions to block.
9) Enable DNS Proxy
When CryptoLocker or other ransomware are launched, it will tamper the DNS Settings of the infected host, in order to be able to contact the servers it needs to work properly. This behaviour can be avoided by activating the DNS Proxy on your Endian device. In this way, all DNS queries from a host behind your Endian will always be intercepted by the Endian, blocking any possibility for CryptoLocker to communicate with its servers.
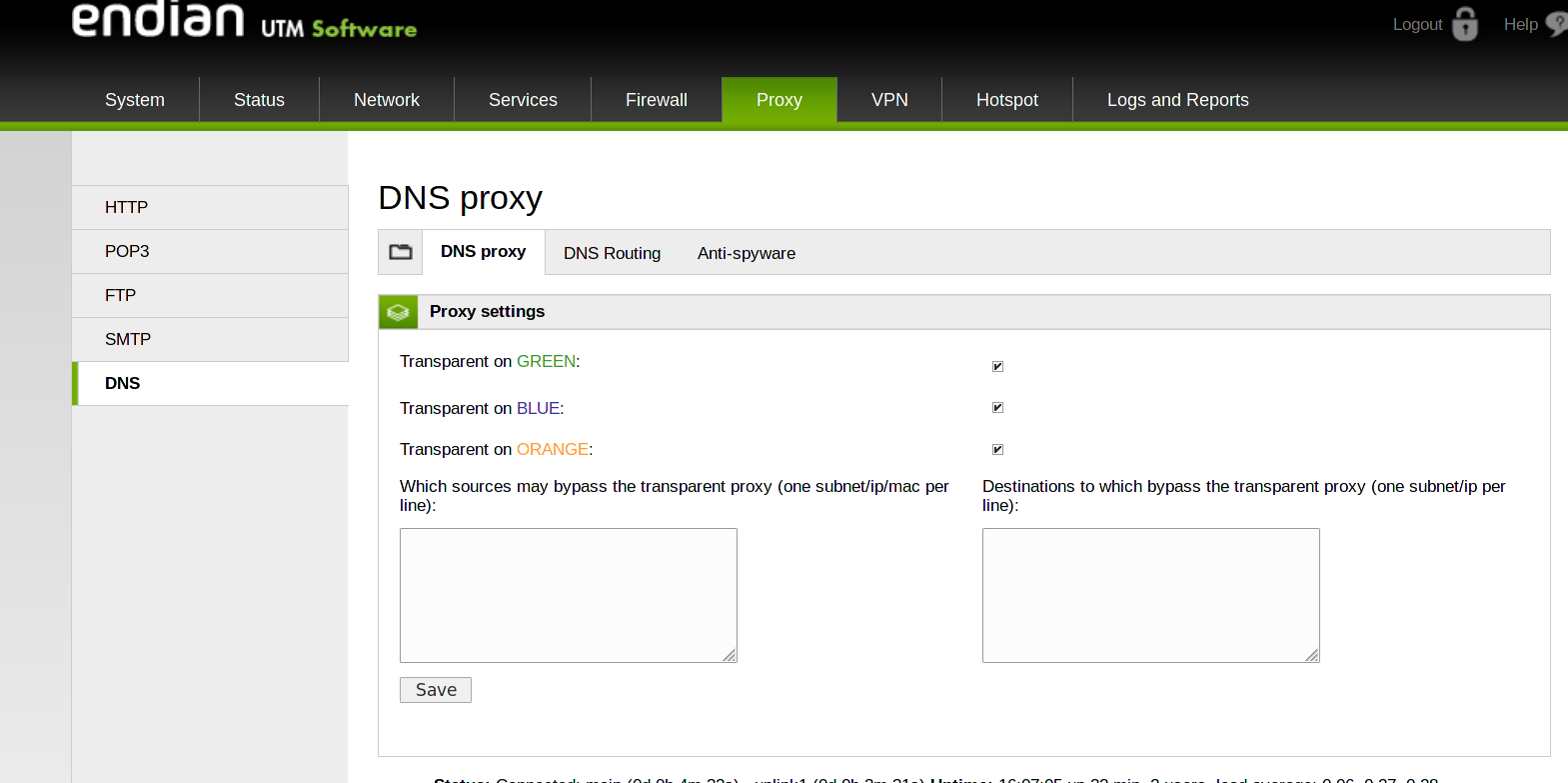
Moreover, the Anti-spyware update should be set to “daily”, to block further known infection domains.
Excellent write-up and thank you for posting.
Very good post!